TL;DR: Missing authentication combined with a simple Insecure Direct Object Reference vulnerability allowed to overtake a selection of temporary locked Instagram accounts. An extrapolation of the PoC account range learned that 4% of all existing & active Instagram accounts (approx. 500 million) were in a vulnerable locked state (approx. 20 million). Facebook fixed the vulnerability within a day and granted a $5.000 bounty 10 days later.
Issue
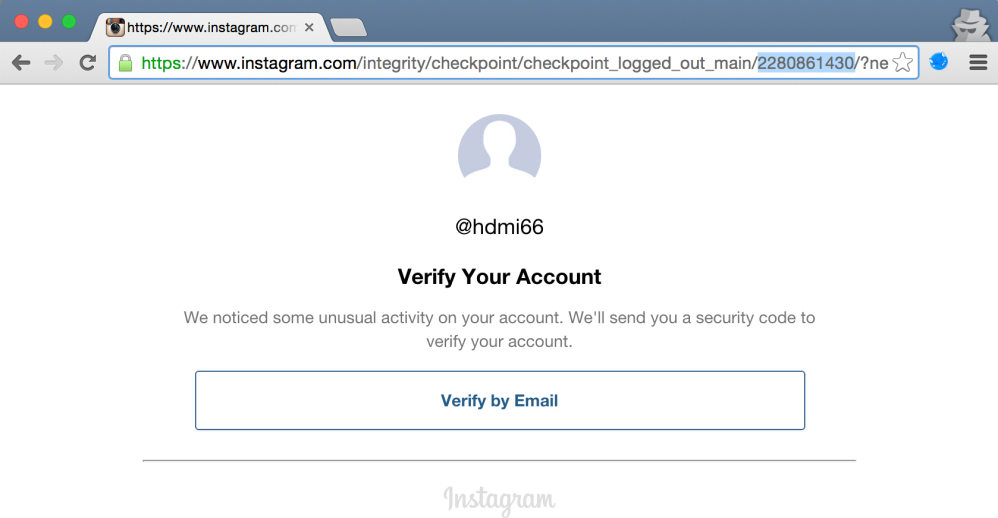
It was a while ago that I actually hunted for vulnerabilities in Instagram when I logged back in to one of my test accounts. I have spent most of my free time in 2016 presenting about Instagram vulnerabilities I found in 2015. After providing valid credentials, I was immediately redirected to a page which told me I had to verify my account, probably due to inactivity. The option that was offered to me was to verify by email, as I didn’t link any phone number to this account yet:
The URL revealed the issue: this page was actually accessible without being authenticated (“checkpoint_logged_out_main”) and contained my Instagram test account’s unique user id. Now, even if I were to land on the same “Verify by Email” page of other accounts, it would have no direct security impact, as I don’t have access to my victims’ email addresses. However, an enumeration of one million accounts in the range 2.000.000000-2.001.000000 (Instagram has incremental user ids 🙂 ) yielded the following interesting results:
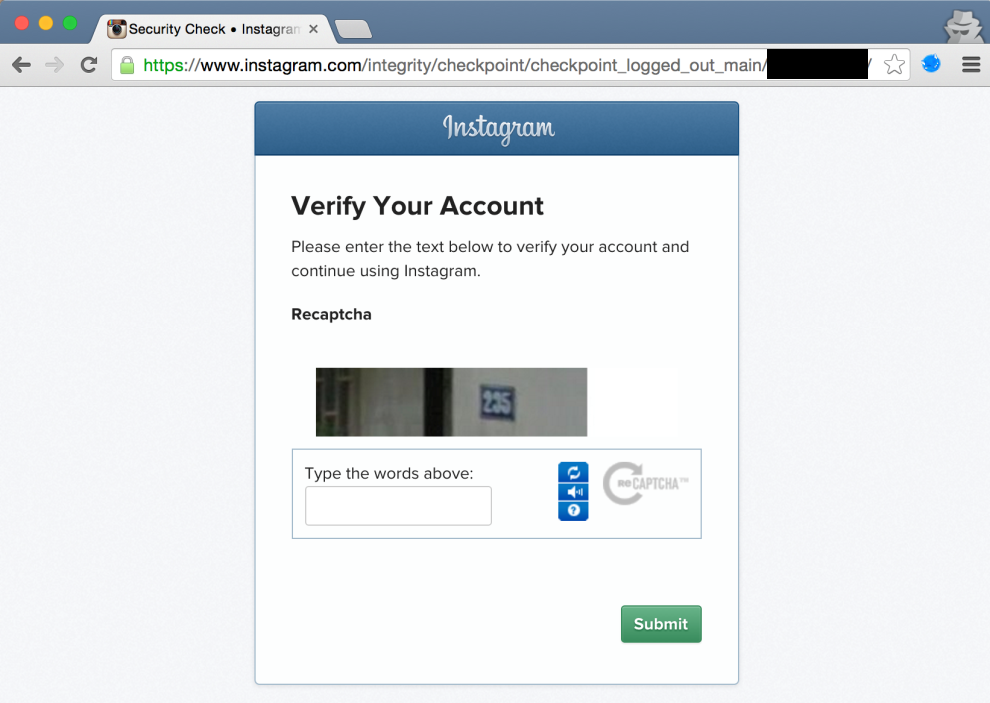
Verify account via Captcha: 1.099 accounts (0.1%)
These might have been accounts that were observed to perform spamming. No direct security impact.
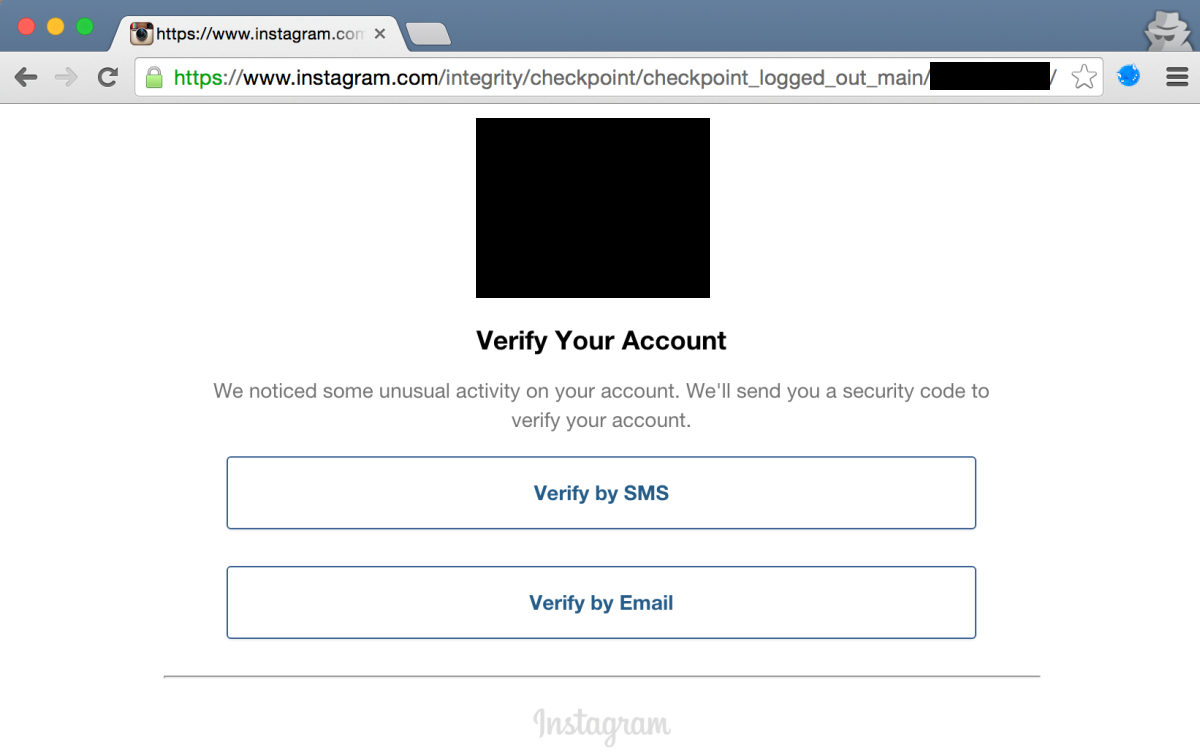
Verify account via email / SMS: 1.960 accounts (0.2%)
This was the same case as for my test account: No direct security impact.
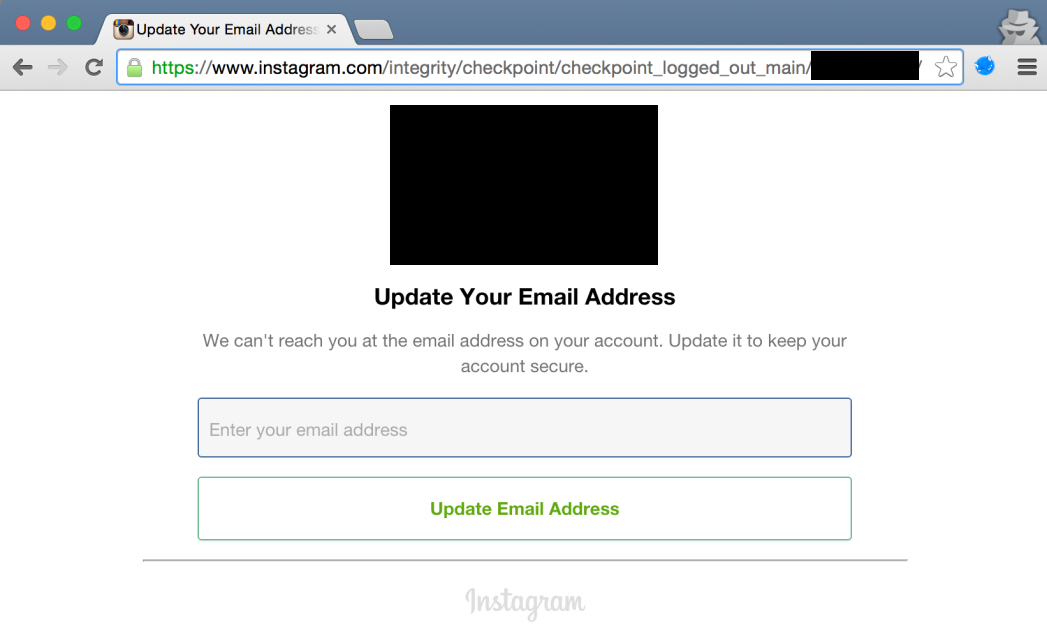
Update email address & verify account: 1.690 accounts (0.17%)
Now this is where things got interesting. This page allowed me to update the email address of the temporary locked account, which is a big deal. Once an attacker could set the email address linked to an Instagram account, he/she could perform a password reset via email and gain full access to it. Big security impact, but only 0.17% accounts affected in the one million range.
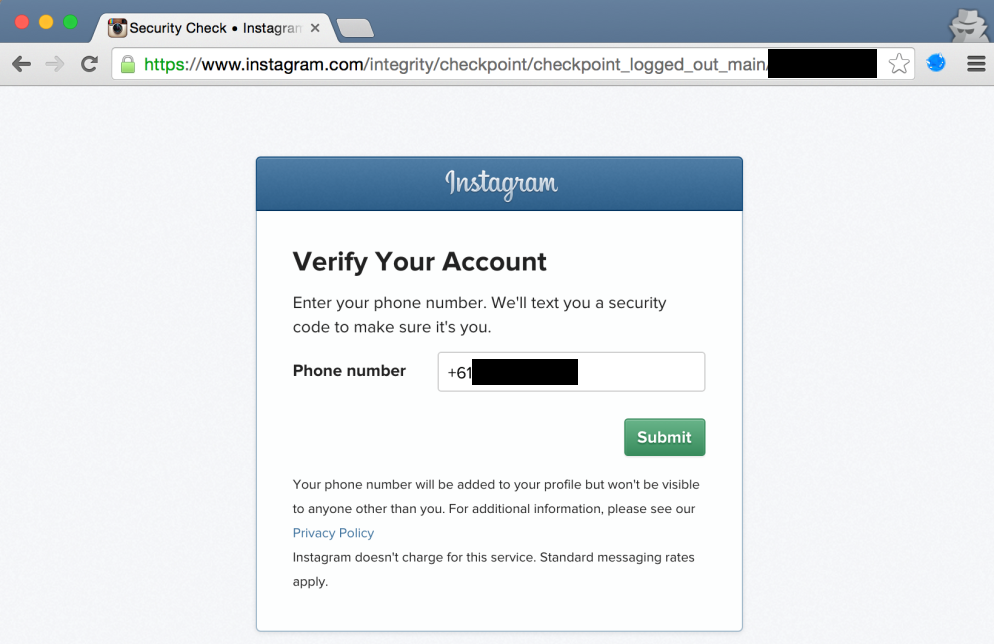
Update phone number & verify account: 38.808 accounts (3.88%)
This case was the most troublesome, as an attacker could on one hand gather sensitive user information (pre-filled phone number in some cases), and on the other hand simply update the phone number linked to the victim Instagram account. After successfully linking a new phone number, an attacker could perform the “reset password via SMS” scenario and gain complete access to the account. Big security impact, and almost 4% of all accounts affected in the one million range. A quick manual verification also learned that these were mostly human accounts which had been inactive for a couple of weeks, of which many had a good amount of followers on Instagram.
Note that I could not immediately get any of my test accounts in the “phone number verification” state and thus did not perform an actual account takeover scenario, since I couldn’t reproduce this on my test accounts directly. This is the only thing you can do when adhering to responsible disclosure – never touch existing accounts! I explicitly mentioned this to Facebook while reporting, in order to avoid any confusion. I believe this is the responsibility of all bug bounty hunters, despite the fact that it might result in lower bounties in some edge cases. The required trust relationship between researchers and bug bounty providers in the eco-system relies on this, which is still too often under pressure currently.
Remediation
Facebook fixed the issue within 24 hours, by enforcing authentication on the pages that allow to update profile information such as email address and/or phone number.
Timeline
- 14/03/2016: Bug submitted to Facebook
- 14/03/2016: Facebook reply: “We are sending it to the appropriate product team for further investigation.”
- 15/03/2016: Facebook reply: “We have looked into this issue and believe that the vulnerability has been patched.”
- 16/03/2016: Confirmation that bug is fixed to Facebook
- 25/03/2016: Facebook reply: “After reviewing the issue you have reported, we have decided to award you a bounty of $5,000 USD.”
What computer languages do you use or learn to find vulnerabilities?
Mostly HTML, JavaScript and scripting languages like Python, Powershell and Bash.